What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-12-20 12:18:46 | WannaCry et Corée du Nord : Qui est Lazarus et quelles sont ses motivations ? (lien direct) |  Alors que la Corée du Nord est accusée d'être directement responsable de l'attaque informatique qui a contaminé plus de 300 000 ordinateurs dans le monde en mai dernier, Proofpoint vient de publier les conclusions de ses dernières recherches mettant en lumière les activités du groupe Lazarus, l'organisation nord-coréenne pointée du doigt dans plusieurs cyberattaques majeures, dont WannaCry. Alors que la Corée du Nord est accusée d'être directement responsable de l'attaque informatique qui a contaminé plus de 300 000 ordinateurs dans le monde en mai dernier, Proofpoint vient de publier les conclusions de ses dernières recherches mettant en lumière les activités du groupe Lazarus, l'organisation nord-coréenne pointée du doigt dans plusieurs cyberattaques majeures, dont WannaCry. |
Wannacry APT 38 | |||
| 2017-12-20 05:18:48 | Greedy North Korean Hackers Targeting Cryptocurrencies and Point-of-Sale Terminals (lien direct) | The North Korean hacking group has turned greedy.
Security researchers have uncovered a new widespread malware campaign targeting cryptocurrency users, believed to be originated from Lazarus Group, a state-sponsored hacking group linked to the North Korean government.
Active since 2009, Lazarus Group has been attributed to many high profile attacks, including Sony Pictures Hack, $81 million
|
Medical | APT 38 | ||
| 2017-12-15 21:04:37 | Lazarus APT Group targets a London cryptocurrency company (lien direct) | >Security experts from Secureworks revealed the Lazarus APT group launched a spearphishing campaign against a London cryptocurrency company. The dreaded Lazarus APT group is back and launched a spearphishing campaign against a London cryptocurrency company to steal employee credentials. The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks […] | Medical | APT 38 | ||
| 2017-12-15 14:00:00 | Things I Hearted This Week 15th December 2017 (lien direct) |
Continuing the trend from last week, I’ll continue trying to put a positive spin on the week’s security news.
Why? I hear you ask. Well, I’ve been mulling over the whole optimist thing, and glass half full analogy and it does work wonders. Side note, a tweet about half full / empty glasses and infosec took on a life of its own a few days ago.
But I’m reminded of the ending monologue by Morgan Freeman in “The Shawshank Redemption”, in which he starts off by saying, “Get busy living or get busy dying.”
So the thought of the week is, “Get busy securing, or get busy insecuring.” Hmm doesn’t quite have the same ring to it. Will have to think of a better word – but you catch my drift. Let’s jump into this week’s interesting security bits
Mirai Mirai on the wall
I picture Brian Krebs as being a Liam Neeson type – he sees that his website is under attack by a never-before seen DDoS attack. He mutters to himself, “I don’t know who you are, but I will hunt you, I will find you, and I will blog about it until you get arrested, prosecuted, and thrown in jail.”
It so happens that this week the hackers behind the Mirai botnet and a series of DDoS attacks pled guilty.
The Hackers Behind Some of the Biggest DDoS Attacks in History Plead Guilty | Motherboard
Mirai IoT Botnet Co-Authors Plead Guilty | KrebsonSecurity
Botnet Creators Who Took Down the Internet Plead Guilty | Gizmondo
Bug Laundering Bounties
 Apparently, HBO negotiated with hackers. Paying them $250,000 under the guise of a bug bounty as opposed to a ransom.
Maybe in time, it will be found that HBO acted above board, maybe it was a sting operation, maybe it was a misconstrued email.
The worrying fact is that any payment exchange system can be used to launder money. However, bug bounty providers don’t (as far as I can tell) have financial services obligations. Does the bug bounty industry need more regulation (shudder)?
Leaked email shows HBO negotiating with hackers | Calgary Herald
Remember the 'Game of Thrones' leak? An Iranian hacker was charged with stealing HBO scripts to raise bitcoin | USA Today
Uber used bug bounty program to launder blackmail payment to hacker | ars Technica
Inside a low budget consumer hardware espionage implant
I’m not much of a hardware expert – actually, I’m not much of a hardware novice either. But this writeup by Mich is awesome. I didn’t even know there were so many ways to sniff, intercept and basically mess around with stuff at such small scale. It’s extremely detailed and I’ve permanently bookmarked it for future reference.
Apparently, HBO negotiated with hackers. Paying them $250,000 under the guise of a bug bounty as opposed to a ransom.
Maybe in time, it will be found that HBO acted above board, maybe it was a sting operation, maybe it was a misconstrued email.
The worrying fact is that any payment exchange system can be used to launder money. However, bug bounty providers don’t (as far as I can tell) have financial services obligations. Does the bug bounty industry need more regulation (shudder)?
Leaked email shows HBO negotiating with hackers | Calgary Herald
Remember the 'Game of Thrones' leak? An Iranian hacker was charged with stealing HBO scripts to raise bitcoin | USA Today
Uber used bug bounty program to launder blackmail payment to hacker | ars Technica
Inside a low budget consumer hardware espionage implant
I’m not much of a hardware expert – actually, I’m not much of a hardware novice either. But this writeup by Mich is awesome. I didn’t even know there were so many ways to sniff, intercept and basically mess around with stuff at such small scale. It’s extremely detailed and I’ve permanently bookmarked it for future reference.
|
Guideline Medical Cloud | Uber APT 38 APT 37 | ||
| 2017-11-22 07:45:40 | Lazarus APT uses an Android app to target Samsung users in the South Korea (lien direct) | >The North Korea linked group Lazarus APT has been using a new strain of Android malware to target smartphone users in South Korea. The hacking campaign was spotted by McAfee and Palo Alto Networks, both security firms attributed the attacks to the Hidden Cobra APT. The activity of the Lazarus APT Group surged in 2014 and 2015, its […] | Medical | APT 38 | ||
| 2017-11-21 09:59:48 | North Korean Hackers Target Android Users in South (lien direct) | At least two cybersecurity firms have noticed that the notorious Lazarus threat group, which many experts have linked to North Korea, has been using a new piece of Android malware to target smartphone users in South Korea. | APT 38 | |||
| 2017-11-20 13:40:00 | North Korea\'s Lazarus Group Evolves Tactics, Goes Mobile (lien direct) | The group believed to be behind the Sony breach and attacks on the SWIFT network pivots from targeted to mass attacks. | APT 38 | |||
| 2017-11-20 12:00:03 | Android Malware Appears Linked to Lazarus Cybercrime Group (lien direct) |  The McAfee Mobile Research team recently examined a new threat, Android malware that contains a backdoor file in the executable and linkable format (ELF). The ELF file is similar to several executables that have been reported to belong to the Lazarus cybercrime group. (For more on Lazarus, read this post from our Advanced Threat Research …
The McAfee Mobile Research team recently examined a new threat, Android malware that contains a backdoor file in the executable and linkable format (ELF). The ELF file is similar to several executables that have been reported to belong to the Lazarus cybercrime group. (For more on Lazarus, read this post from our Advanced Threat Research …
|
APT 38 | ★★★★★ | ||
| 2017-11-15 17:21:07 | US Government Warns of Hidden Cobra North Korea Cyber Threat (lien direct) | A Department of Homeland Security (DHS) Alert released on Tuesday warns the public about a campaign of hacking by the government of North Korea it has code-named “Hidden Cobra.” DHS joined the FBI for a joint Technical Alert about the campaign and its use of a piece of malicious software dubbed FallChill, a remote access trojan (RAT)...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/493009316/0/thesecurityledger -->» | Medical | APT 38 | ||
| 2017-11-15 11:14:56 | US Government issues alert about North Korean "Hidden Cobra" cyber attacks (lien direct) |  The FBI and US Department of Homeland Security have issued an alert that hackers have targeted the aerospace industry, financial services and critical infrastructure with a remote access trojan (RAT) to further exploit vulnerable networks. The FBI and US Department of Homeland Security have issued an alert that hackers have targeted the aerospace industry, financial services and critical infrastructure with a remote access trojan (RAT) to further exploit vulnerable networks.
|
Medical | APT 38 | ||
| 2017-11-15 08:52:11 | US DHS and FBI share reports on FALLCHILL and Volgmer malware used by North Korean Hidden Cobra APT (lien direct) | >US DHS published the details of the malware FALLCHILL and Volgmer used by the APT group Hidden Cobra that is linked to the North Korean government. The US Department of Homeland Security (DHS) published the details of the hacking tool FALLCHILL used one of the APT group linked to the North Korean government tracked as Hidden Cobra (aka Lazarus Group). […] | Medical | APT 38 | ||
| 2017-10-18 07:04:09 | BAE Systems report links Taiwan heist to North Korean LAZARUS APT (lien direct) | >Researchers at BAE Systems investigated the recent cyber-heist that targeted a bank in Taiwan and linked the action to the notorious Lazarus APT group. The activity of the Lazarus APT Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated. […] | APT 38 | |||
| 2017-10-17 07:50:25 | North Korean Hackers Used Hermes Ransomware to Hide Recent Bank Heist (lien direct) | Evidence suggests the infamous Lazarus Group, a hacking crew believed to be operating out of North Korea, is behind the recent hack on the Far Eastern International Bank (FEIB) in Taiwan. [...] | Medical | APT 38 | ||
| 2017-10-16 22:32:36 | Taiwan Heist: Lazarus Tools and Ransomware (lien direct) | Written by Sergei Shevchenko, Hirman Muhammad bin Abu Bakar, and James WongBACKGROUNDReports emerged just over a week ago of a new cyber-enabled bank heist in Asia. Attackers targeting Far Eastern International Bank (FEIB), a commercial firm in Taiwan, moved funds from its accounts to multiple overseas beneficiaries. In a story which reminds us of the Bangladesh Bank case – the culprits had compromised the bank's system connected to the SWIFT network and used this to perform the transfers. In recent days, various malware samples have been uploaded to malware repositories which appear to originate from the intrusion. These include both known Lazarus group tools, as well as a rare ransomware variant called 'Hermes' which may have been used as a distraction or cover-up for the security team whilst the heist was occurring. The timeline below provides an overview of the key events: 01 October 2017  Malware compiled containing admin credentials for the FEIB network. 03 October 2017 Malware compiled containing admin credentials for the FEIB network. 03 October 2017  Transfers using MT103 messages were sent from FEIB to Cambodia, the US and Sri Lanka. Messages to cover the funds for the payments were incorrectly created and sent. 03 October 2017 Transfers using MT103 messages were sent from FEIB to Cambodia, the US and Sri Lanka. Messages to cover the funds for the payments were incorrectly created and sent. 03 October 2017  Breach discovered and ransomware uploaded to online malware repository site. 04 October 2017 Breach discovered and ransomware uploaded to online malware repository site. 04 October 2017  Individual in Sri Lanka cashes out a reported Rs30m (~$195,000). 06 October 2017 Individual in Sri Lanka cashes out a reported Rs30m (~$195,000). 06 October 2017  |
Medical | Wannacry APT 38 | ||
| 2017-08-16 16:55:51 | North Korean Cyberspies Target US Defense Contractors Following Nuclear Threats (lien direct) | The North Korean cyber-espionage group known as the Lazarus Group has been busy hacking US defense contractors, according to a report published on Monday by security research firm Palo Alto Networks. [...] | Medical | APT 38 | ||
| 2017-08-14 14:51:02 | North Korea-Linked Hackers Target U.S. Defense Contractors (lien direct) | The North Korea-linked cyber espionage group known as Lazarus is believed to be behind attacks targeting individuals involved with United States defense contractors, Palo Alto Networks reported on Monday. | APT 38 | |||
| 2017-06-21 11:47:47 | WannaCryptor attack \'may have come from Lazarus group\' (lien direct) | Experts in the UK and the US have reportedly claimed that the recent global WannaCryptor ransomware attack was initiated by the North Korean Lazarus Group. | Medical | Wannacry APT 38 | ||
| 2017-06-19 08:15:46 | Hidden Cobra And DeltaCharlie: An Explainer (lien direct) | The ISBuzz Post: This Post Hidden Cobra And DeltaCharlie: An Explainer | Medical | APT 38 | ||
| 2017-06-16 16:00:31 | Threatpost News Wrap, June 16, 2017 (lien direct) | Mike Mimoso and Chris Brook discuss the news of the week, including Microsoft's XP patches, Hidden Cobra, a Nigerian BEC campaign, MacRansom, and more. | Medical | APT 38 | ||
| 2017-06-14 17:55:58 | US Blames North Korean \'Hidden Cobra\' Group For Cyber Attacks Since 2009 (lien direct) | The ISBuzz Post: This Post US Blames North Korean ‘Hidden Cobra’ Group For Cyber Attacks Since 2009 | Medical | APT 38 | ||
| 2017-06-14 17:17:21 | DHS, FBI Warn of North Korea \'Hidden Cobra\' Strikes Against US Assets (lien direct) | DHS and the FBI warned that North Korean attackers are targeting U.S. businesses with malware- and botnet-related attacks that are part of concerted effort dubbed "Hidden Cobra." | Medical | APT 38 | ||
| 2017-06-14 14:22:31 | US indicts North Korea for host of cyberattacks, expects more to come (lien direct) | A North Korean entity called Hidden Cobra was behind a series of cyberattacks in the US using sophisticated tools and targeting a diverse group of entities. | Medical | APT 38 | ||
| 2017-06-14 10:44:45 | U.S. Warns of North Korea\'s \'Hidden Cobra\' Attacks (lien direct) | The United States Computer Emergency Readiness Team (US-CERT) released a technical alert on Tuesday on behalf of the DHS and the FBI to warn organizations of North Korea's “Hidden Cobra†activities, particularly distributed denial-of-service (DDoS) attacks. | Medical | APT 38 | ||
| 2017-06-14 05:23:04 | US Warns of \'DeltaCharlie\' – A North Korean DDoS Botnet Malware (lien direct) | The United States government has released a rare alert about an ongoing, eight-year-long North Korean state-sponsored hacking operation.
The joint report from the FBI and U.S. Department of Homeland Security (DHS) provided details on "DeltaCharlie," a malware variant used by "Hidden Cobra" hacking group to infect hundreds of thousands of computers globally as part of its DDoS botnet network.
|
Medical | APT 38 | ||
| 2017-06-14 04:00:00 | Video: North Korean hacking group has been hitting the US since 2009 (lien direct) | Hidden Cobra, a North Korean-backed hacking group, may also be responsible for WannaCry and the Sony Pictures hack. | Medical | Wannacry APT 38 | ★★★★ | |
| 2017-05-31 07:33:02 | Analysis of Competing Hypotheses, WCry and Lazarus (ACH part 2), (Wed, May 31st) (lien direct) | Introduction In my previous diary, I did a very brief introduction on what the ACH method is [1], so that now all readers, also those who had never seen it before, can have a common basic understanding of it. One more thing I have not mentioned yet is how the scores are calculated. There are three different algorithms: an Inconsistency Counting algorithm, a Weighted Inconsistency Counting algorithm, and a Normalized algorithm [2]. The Weighted Inconsistency Counting algorithm, the one used in todays examples, builds on the Inconsistency algorithm, but also factors in weights of credibility and relevance values. For each item of evidence, a consistency entry of I width:300px" /> Today, I will apply ACH to a recent quite known case: WCry attribution. There has been lots of analyses and speculations around it, lately several sources in the InfoSec community tied WCry strongly to Lazarus Group [3][4][5][6], while some others provided motivation for being skeptical about such attribution [7]. Therefore, it is a perfect case to show the use of ACH: several different hypotheses, facts, evidences and assumptions. Digital Shadows WCry ACH analysis About two weeks ago, Digital Shadows published a very well done post on ACH applied to WCry attribution [8]. Regarding possible attribution to Lazarus though, as stated on their post, At the time of writing, however, we assessed there to be insufficient evidence to corroborate this claim of attribution to this group, and alternative hypotheses should be considered. Therefore among the hypotheses considered is missing one specifically for Lazarus in place of a more generic nation state or state affiliate actor. The following are the four different hypotheses considered by Digital Shadows: A sophisticated financially-motivated cybercriminal actor - H1 An unsophisticated financially-motivated cybercriminal actor - H2 A nation state or state-affiliated actor conducting a disruptive operation - H3 A nation state or state-affiliated actor aiming to discredit the National Security Agency (NSA) width:600px" /> Given the final scores computed, they have assessed that though by no means definitive, a WannaCry campaign launched by an unsophisticated cybercriminal actor was the most plausible scenario based on the information that is currently available. Just one note on my side, from my calculation seems they have made a mistake, and H2 score should be -2.121 rather than -1.414. This does not change the final result, but brings H2 and H3 way closer. My WCry ACH Analysis Although the Digital Shadows analysis was a very good one, I felt something was missing, both on the hypotheses as well as on the evidences side. Particularly, in my opinion, I would add three more hypotheses. When thinking about NSA being the final target of this, other than A nation state or state-affiliated actor aiming to discredit the NSA, I think that it should be considered also a (generic/unattributed) TA aiming at unveiling/exposing the extent of possible NSA network of compromised machines (H5). This is something one would expect from a hacktivist maybe, although it seems to be way more sophisticated than what hacktivist have got us used to. One difference with the H4 could be on the lack of supporting media narrative. While if one wants to discredit NSA would be ready to have a supporting media narrative, if the goal was simply to unveil and show to everyone the potential extent of NSA infected machines, the infection as it was would have been sufficient, given also the abundant media coverage it got. Although this may still be seen as too close to H4 to be a different hypothesis, I still do see a case for it. | Medical | Wannacry APT 38 | ||
| 2017-05-30 15:55:19 | Latest WannaCry Theory: Currency Manipulation (lien direct) | The recent WannaCry outbreak is still a mystery. We know what (ransomware), and how (a Windows vulnerability on unsupported or unpatched systems); but we don't know who or why. We're not short of theories: Lazarus, North Korea, some other nation-state actor, Chinese or Russian actors -- but none of these has gained general acceptance. | Wannacry APT 38 | |||
| 2017-05-30 14:00:19 | New Evidence Cements Theory That North Korea is Behind Lazarus Group (lien direct) | A 53-page report released today by Group-IB, a Russian cyber-security vendor, contains new evidence that cements the theory that the North Korean government is behind the Lazarus Group, a cyber-espionage outfit. [...] | Medical | APT 38 | ||
| 2017-05-29 11:10:00 | Linguistic Analysis Suggests WannaCry Hackers Could be From Southern China (lien direct) | It's been almost four weeks since the outcry of WannaCry ransomware, but the hackers behind the self-spread ransomware threat have not been identified yet.
However, two weeks ago researchers at Google, Kaspersky Lab, Intezer and Symantec linked WannaCry to 'Lazarus Group,' a state-sponsored hacking group believed to work for the North Korean government.
Now, new research from dark web
|
Medical | Wannacry APT 38 | ||
| 2017-05-23 11:11:31 | WannaCry \'Highly Likely\' Work of North Korean-linked Hackers, Symantec Says (lien direct) | North Korea-linked Lazarus Hacking Group is "Highly Likely" to be Responsible for the Global "WannaCry" Ransomware Attack, Symantec Says | Wannacry APT 38 | |||
| 2017-05-23 10:35:15 | WannaCry connection to North Korea hacking group \'compelling\' (lien direct) | WannaCry, the ransomware that spread through the UK's National Health Service and companies around the world, shows “compelling evidence†of a link to North Korean hacking group Lazarus, according to a new report by Symantec.  The cyber security company believes there is a “close connection†to Lazarus, the group behind the cyber attacks on Sony ... | Wannacry APT 38 | ★★ | ||
| 2017-05-23 08:30:40 | WannaCry : de nouveaux indices pointent vers la Corée du Nord (lien direct) | Une société de sécurité informatique a enquêté sur l'attaque WannaCry. Elle a détecté plusieurs indices mettant en cause le groupe de hackers Lazarus, lié à la Corée du Nord.  |
Wannacry APT 38 | |||
| 2017-05-22 22:19:59 | WannaCry: Ransomware attacks show strong links to Lazarus group (lien direct) | Similarities in code and infrastructure indicate close connection to group that was linked to Sony Pictures and Bangladesh Bank attacks | Wannacry APT 38 | |||
| 2017-05-19 13:00:19 | Threatpost News Wrap, May 19, 2017 (lien direct) | Mike Mimoso and Chris Brook discuss WannaCry, Microsoft's response, the killswitches, a potential link with Lazarus Group, and what the future holds for the ShadowBrokers. | Medical | Wannacry APT 38 | ||
| 2017-05-17 06:50:12 | 3 Security Firms Say WannaCry Ransomware Shares Code with North Korean Malware (lien direct) | While initially, we thought this would be a silly and unsubstantiated discovery, the number of security firms claiming they've identified and confirmed connections between the WannaCry ransomware and malware used by the Lazarus Group has now gone up to three. [...] | Medical | Wannacry APT 38 | ||
| 2017-05-17 03:33:55 | WanaCrypt0r Ransomworm (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDSince the release of the ETERNALBLUE exploit by 'The Shadow Brokers' last month security researchers have been watching for a mass attack on global networks. This came on Friday 12th May when it was bundled with ransomware called WanaCrypt0r and let loose. Initial reports of attacks were highlighted by Telefonica in Spain but the malware quickly spread to networks in the UK where the National Health Service (NHS) was impacted, followed by many other networks across the world.The infographic below illustrates the key components of the WanaCrypt0r ransomware. This is described in further detail in subsequent sections of this report along with initial clues on attribution.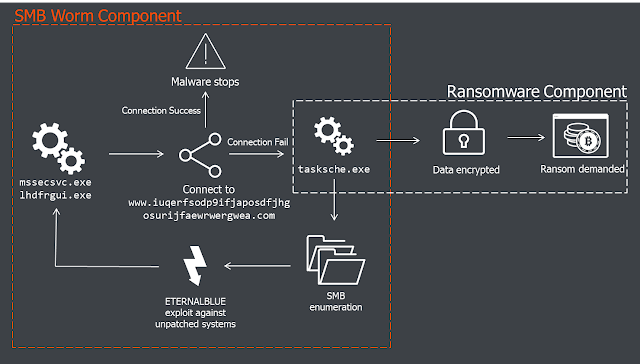 ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs |
Guideline Medical | Wannacry APT 38 | ||
| 2017-05-16 15:45:50 | WannaCry Shares Code with Lazarus APT Samples (lien direct) | Experts have confirmed there are similarities between code used by the ransomware WannaCry and the Lazarus APT. | Wannacry APT 38 | |||
| 2017-05-16 10:39:48 | WannaCry ransomware cyber-attack \'may have N Korea link\' (lien direct) | You may not have heard of the Lazarus Group, but you may be aware of its work. The devastating hack on Sony Pictures in 2014, and another on a Bangladeshi bank in 2016, have both been attributed to the highly sophisticated group. It is widely believed that the Lazarus Group worked out of China, but on behalf ... | Medical | Wannacry APT 38 | ||
| 2017-05-16 08:01:19 | La Corée du Nord serait derrière l\'attaque WannaCry (lien direct) | Des indices techniques pointent vers le groupe de pirates Lazarus, connu pour le cybersabotage de Sony Pictures et qui seraient lié au régime de Pyongyang.  |
Wannacry APT 38 | ★★★★★ | ||
| 2017-04-05 14:15:00 | Matching Wits with a North Korea-Linked Hacking Group (lien direct) | Skilled 'Bluenoroff' arm of infamous Lazarus hacking team behind Bangladesh Bank heist and Sony attacks actively resists investigators on its trail, Kaspersky Lab says. | APT 38 | |||
| 2017-04-04 22:20:41 | À la poursuite de " Lazarus " (lien direct) | À la poursuite de " Lazarus " : sur les traces du groupe chasseur de grandes banques internationales Kaspersky Lab... Cet article À la poursuite de " Lazarus " est diffusé par Data Security Breach. | APT 38 | |||
| 2017-04-04 08:22:00 | Kaspersky Lab reveals \'direct link\' between banking heist hackers and North Korea (lien direct) | Kaspersky Lab found a “direct link†between the Lazarus group banking heist hackers and North Korea.While Lazarus is a notorious cyber-espionage and sabotage group, a subgroup of Lazarus, called Bluenoroff by Kaspersky researchers, focuses only on financial attacks with the goal of “invisible theft without leaving a trace.â€The group has four main types of targets: financial institutions, casinos, companies involved in the development of financial trade software and crypto-currency businesses.To read this article in full or to leave a comment, please click here | Medical | APT 38 | ||
| 2017-04-03 22:53:52 | Security Analyst Summit 2017 Day One Recap (lien direct) | Mike Mimoso and Chris Brook recap the first day of this year's Security Analyst Summit, including Mark Dowd's memory corruption bug keynote, the digital archeology around Moonlight Maze, ATM hacking, and the Lazarus APT. | APT 38 | |||
| 2017-04-03 20:38:44 | Lazarus APT Spinoff Linked to Banking Hacks (lien direct) | The Lazarus Group has splintered off a group whose mission is to attack banks and steal money in order to fund its operations. | Medical | APT 38 | ||
| 2017-04-03 18:33:00 | Hackers responsible for $80M bank heist show \'no signs of stopping\' (lien direct) | Lazarus, linked to the famous Bangladeshi bank heist, is probing Southeast Asia and Europe in the hunt for fresh targets. | APT 38 | |||
| 2017-04-03 16:33:01 | Banking hackers left a clue that may link them to North Korea (lien direct) | The notorious hackers behind a string of banking heists have left behind a clue that supports a long-suspected link to North Korea, according to security researchers.The so-called Lazarus Group has been eyed as a possible culprit behind the heists, which included last February's $81 million theft from Bangladesh's central bank through the SWIFT transaction software.However, hackers working for the group recently made a mistake: They failed to wipe the logs from a server the group had hacked in Europe, security firm Kaspersky Lab said on Monday.To read this article in full or to leave a comment, please click here | Medical | APT 38 | ||
| 2017-03-17 14:10:00 | North Korea\'s \'Lazarus\' Likely Behind New Wave of Cyberattacks (lien direct) | Symantec says it has digital evidence that hack group Lazarus is behind the recent sophisticated cyberattacks on 31 countries. | APT 38 | |||
| 2017-03-06 12:13:22 | Lazarus & Watering-hole attacks (lien direct) | On 3rd February 2017, researchers at badcyber.com released an article that detailed a series of attacks directed at Polish financial institutions. The article is brief, but states that "This is – by far – the most serious information security incident we have seen in Poland" followed by a claim that over 20 commercial banks had been confirmed as victims.This report provides an outline of the attacks based on what was shared in the article, and our own additional findings. ANALYSISAs stated in the blog, the attacks are suspected of originating from the website of the Polish Financial Supervision Authority (knf.gov[.]pl), shown below: From at least 2016-10-07 to late January the website code had been modified to cause visitors to download malicious JavaScript files from the following locations: hxxp://sap.misapor[.]ch/vishop/view.jsp?pagenum=1hxxps://www.eye-watch[.]in/design/fancybox/Pnf.action Both of these appear to be compromised domains given they are also hosting legitimate content and have done for some time. The malicious JavaScript leads to the download of malware to the victim's device. Some hashes of the backdoor have been provided in BadCyber's technical analysis: 85d316590edfb4212049c4490db08c4bc1364bbf63b3617b25b58209e4529d8c1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae The C&Cs given in the BadCyber analysis were the following IP addresses: 125.214.195.17196.29.166.218 LAZARUS MALWAREOnly one of the samples referenced by BadCyber is available in public malware repositories. At the moment we cannot verify that it originated from the watering-hole on the KNF website – but we have no reason to doubt this either. MD5 hash Filename File Info First seen From at least 2016-10-07 to late January the website code had been modified to cause visitors to download malicious JavaScript files from the following locations: hxxp://sap.misapor[.]ch/vishop/view.jsp?pagenum=1hxxps://www.eye-watch[.]in/design/fancybox/Pnf.action Both of these appear to be compromised domains given they are also hosting legitimate content and have done for some time. The malicious JavaScript leads to the download of malware to the victim's device. Some hashes of the backdoor have been provided in BadCyber's technical analysis: 85d316590edfb4212049c4490db08c4bc1364bbf63b3617b25b58209e4529d8c1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae The C&Cs given in the BadCyber analysis were the following IP addresses: 125.214.195.17196.29.166.218 LAZARUS MALWAREOnly one of the samples referenced by BadCyber is available in public malware repositories. At the moment we cannot verify that it originated from the watering-hole on the KNF website – but we have no reason to doubt this either. MD5 hash Filename File Info First seen |
Guideline Medical | APT 38 | ||
| 2017-03-06 12:13:03 | Lazarus\' False Flag Malware (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDWe continue to investigate the recent wave of attacks on banks using watering-holes on at least two financial regulator websites as well as others. Our initial analysis of malware disclosed in the BadCyber blog hinted at the involvement of the 'Lazarus' threat actor. Since the release of our report, more samples have come to light, most notably those described in the Polish language niebezpiecznik.pl blog on 7 February 2017. MD5 hash Filename Compile Time File Info Submitted 9216b29114fb6713ef228370cbfe4045 srservice.chm N/A N/A N/A 8e32fccd70cec634d13795bcb1da85ff srservice.hlp N/A N/A N/A e29fe3c181ac9ddb | Guideline Medical | APT 38 | ||
| 2017-02-23 14:30:47 | Smashing Security #009: False flags and hacker clues (lien direct) |  The Lazarus malware attempts to trick you into believing it was written by Russians, second-hand connected cars may be easier to steal, and is your child a malicious hacker?
All this and more is discussed in the latest podcast by computer security veterans Graham Cluley, Vanja Svajcer and Carole Theriault.
Oh, and Carole gets Graham and Vanja to apologise for mistakes of their past... The Lazarus malware attempts to trick you into believing it was written by Russians, second-hand connected cars may be easier to steal, and is your child a malicious hacker?
All this and more is discussed in the latest podcast by computer security veterans Graham Cluley, Vanja Svajcer and Carole Theriault.
Oh, and Carole gets Graham and Vanja to apologise for mistakes of their past...
|
APT 38 |
To see everything:
Our RSS (filtrered)
